אבטחת חשבונות משתמשים ומחשבים
חזקו את האבטחה הפנימית שלכם על ידי אכיפת מדיניות Zero Trust ומעקב אחרי כל המכשירים שלכם.
הקפיצו את רמת האבטחה בארגונכם
יצרנו שותפויות חזקות עם ספקי התוכנה המובילים בעולם כדי להציע לכם פתרונות אבטחה שאנחנו מאמינים בהם בלב שלם. החל מהגנה על מחשבי העובדים ועד לניהול וארגון חשבונות שירות בעלי הרשאות גבוהות, אנו נסייע לארגון שלכם לצמצם את כל משטחי ההתקפה האפשריים – חיצוניים ופנימיים כאחד.
מוצרים:
Absolute Secure Endpoint - Resilience: אבטחת מחשבים מוטמעת ב-BIOS
הגנו על המכשירים, היישומים והנתונים שלכם. ודאו עמידות בפני איומי סייבר עבור נקודות הקצה והיישומים הקריטיים שלכם.
הידעת? המכשיר שלכם כבר כולל את טכנולוגיית האבטחה המלאה של Absolute! מעל ל-600 מיליון מכשירים ברחבי העולם מגיעים עם Absolute Persistence® מוטמע בליבה שלהם.
בקדמת עמידות נקודות הקצה, Absolute היא מובילה עולמית, המציעה פתרונות שמאפשרים לארגון שלכם לשרוד ולהתאושש מאיומי סייבר ותקיפות על מחשבי הקצה והיישומים הקריטיים המותקנים.
יכולות:

ניטור "בריאות" יישומים
קבו אחר אינדיקטורים קריטיים לבריאות של 2,000 יישומי Windows ו-Mac החיוניים לעסק, לפרודוקטיביות ולאבטחה. זיהו כשלים וחקרו את הסיבות מאחוריהם.

ריפוי עצמי של תוכנות קריטיות
השתמשו ב-Application Resilience כדי לתקן או להתקין מחדש יישומים חיוניים באופן אוטומטי אם הם מושבתים או לא פועלים כראוי. גם אם משתמש הסיר באופן יזום את תוכנת האנטי-וירוס למשל, יכולות הריפוי העצמי של Absolute יוודאו שעל כל מחשב יותקנו כל תוכנות האבטחה המוגדרות אצלו במדיניות.

רמידיאציה ושחזור מרחוק
שפרו את יכולות התגובה והשחזור שלכם באמצעות סקריפטים מותאמים אישית על פני מכשירים. התמודדו עם אתגרים כמו נקודות קצה ללא תקשורת, מתקפות כופר ופגיעויות באמצעות אוטומציה עם סקריפטים מותאמים אישית או מוכנים מראש של Absolute Reach.
עודפחות יכולות

Detect device movement
Create geofences to detect any unauthorized device movements, triggering alerts whenever a device crosses a predefined boundary.

Freeze devices at risk
Activate remote device freezing upon threat detection, and provide users with a personalized message automatically or upon request.
![]()
Selectively delete sensitive data
Selectively delete files on any device anywhere, or even completely wipe out the device according to NIST 800-88 with compliance certificate.

Recover stolen devices
Locate and retrieve stolen devices with the Absolute Investigation team experts in collaboration with local law enforcement.
למדו עוד על Absolute Secure Endpoint:
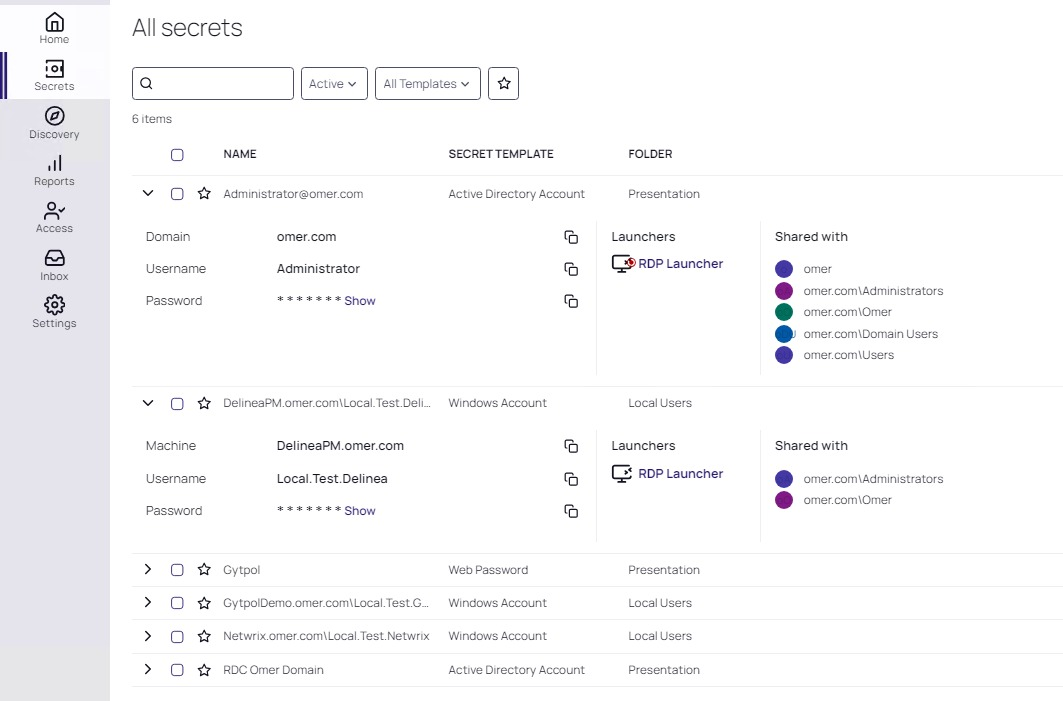
Secret Sever: תוכנת PAM מהמתקדמות בעולם
שפרו את הגנת החשבונות הפריווילגים שלכם עם פתרון Privileged Access Management (PAM) המוביל בתעשייה.
Secret Server בולט ככספת Privileged Access Management הטובה ביותר בשוק, מועדפת על מנהלי IT ואנשי אבטחת מידע בזכות קלות השימוש, עלות כוללת נמוכה ותכונות מתקדמות. מככב כ-Leader ב-Gartner כבר שנה שישית ברציפות.
הפיקו ערך מהיר ביותר עם Secret Server, זמין לפריסה בענן ו-on-premises. עם יכולות ותמחור מדורגים, Secret Server Cloud ו-Secret Server On-premise מספקים את הגמישות להתאים לדרישות שלכם, וכל זאת תוך שיפור האבטחה, היעילות והפרודוקטיביות.
יכולות:

כספת מאובטחת
אבטחו את ה-credentials הפריווילגים שלכם בכספת מרכזית ומוצפנת. בין אם מדובר בפרטי משתמשי Active Directory, משתמשים מקומיים, חשבונות SAP או חשבונות משתמשם לאתרים ברשת, Secret Server מציע קרוב ל-60 תבניות אישורים, ומבטיח כיסוי מקיף לאישורים רגישים.

גלו חשבונות פריוולגים בארגון
זהו באמצעות תהליך אוטומטי את כל חשבונות השירות, היישומים, המנהלים וה-root כדי למנוע התפשטות של תוקף פוטנציאלי, והביטו במבט כולל על כל המשתמשים הפריווילגים בארגון.

אוטומציה ודלגציה
החליפו סיסמאות של משתמשים פריוולגים באופן אוטומטי, הזריקו לתוך ה-Services של כל חשבון, אכפו סטנדרטים של מורכבות סיסמה וטפלו בתלויות (dependencies) בצורה חלקה. הטמיעו תהליכי אישור לבקשות גישה. בקרת גישה מאפשרת אכיפה וניהול של מדיניות "המינימום הנדרש", המבטיחה שלמשתמשים תינתן גישה רק למה שחיוני לתפקידם.
עודפחות יכולות

Control sessions
Integrate session launching, proxies, monitoring, and recording functionalities. Efficiently record sessions with screen and keystroke recording features. Utilize Session Monitoring to gain real-time insight into all privileged user sessions initiated from Secret Server, allowing administrators to monitor active sessions, terminate risky or unauthorized ones promptly, or directly communicate with users.

Enhance reporting and compliance
Streamline auditing, alerting, and reporting processes to meet regulatory standards and showcase compliance to internal and external auditors. Benefit from out-of-the-box and customizable reporting features, making executive reviews and audits hassle-free.
צפו ב-Secret Server בפעולה:
Privilege Manager: בקרה ושליטה על תחנות קצה (EPM)
תוכנה לניהול פריווילגיות בתחנות קצה, ושליטה ביישומים.
צמצמו את הסיכון לתוכנות זדוניות ואיומי אבטחה מודרניים המנצלים יישומים על ידי הסרת הרשאות מנהל מקומי ואכיפת מדיניות "המינימום הנדרש" בנקודות הקצה.
יכולות:

אבטחה מקומית
השתלטו על אבטחת נקודות הקצה המקומיות ויישמו גישה מבוססת מדיניות של "המינימום הנדרש". נהלו ביעילות משתמשים וקבוצות מקומיים, שלטו בהרשאות מנהל מקומי ואוטומטו את החלפת הסיסמאות. השתמשו ב-Privilege Manager כדי להסיר אוטומטית את כל ההרשאות המנהליות המקומיות בנקודות הקצה, ולהבטיח עמידה במדיניות "המינימום הנדרש". עם העלאת הרשאות ברמת היישום, משתמשים יכולים לגשת למערכות הדרושות להם מבלי לקבל הרשאות מוגבהות ברמת המשתמש.

שליטה ביישומים
נהלו כל יישום בנקודות הקצה שלכם עם מדיניות מותאמת אישית, הכוללת חוקי אישור/חסימה והגבלה/העלאה דינמיים, ניתוח יישומים בזמן אמת, תהליכי אישור הרשאות ועוד. השתמשו במדיניות המוכנה לשימוש של Privilege Manager, או התאימו כל פרט לצרכים שלכם.

ניטור ודיווח
Privilege Manager מציע לוח בקרה מרכזי לדיווח המאפשר הערכה מהירה של מצב נקודות הקצה, יומני פעילות ונתוני אירועים. עם ספריית דוחות מקיפה, לוח בקרה זה, רספונסיבי וניתן להתאמה אישית, מאפשר לכם לנתח דוחות לפי ממדים שונים כגון זמן, אזור גיאוגרפי, מערכת הפעלה ומצב. בנוסף, ניתן להגדיר התרעות אוטומטיות ישירות מלוח הבקרה כדי להתעדכן על בעיות פוטנציאליות.
צפו ב-Privilege Manager בפעולה:
Account Lifecycle Manager: ניהול חשבונות שירות בפשטות
פשטו את ניהול חשבונות השירות בצורה חלקה, מהגילוי וההקצאה ועד לסיום חיי המשתמש.
השיגו תמונה מלאה של משטח ההתקפות המועדף שלכם וצמצמו את הסיכונים הקשורים לניהול מחזור חיים של חשבונות שירות.
עם Account Lifecycle Manager, תוכלו להתמודד בצורה יעילה עם התפשטות חשבונות השירות תוך שליטה עליהם באמצעות תהליכי עבודה ופונקציות אוטומטיות להקצאת הרשאות, ניהול, קומפליינס, וסיום חיי המשתמש.
יכולות:

הגדרת תהליכי עבודה (workflows)
הגדירו תהליכי הקצאה (provisioning) עם הגדרות אישור מותאמות אישית לכל סוג בקשת חשבון. האינטגרציה הדו-כיוונית עם ServiceNow מחברת בצורה חלקה את ניהול חשבונות השירות לתהליכי העבודה של IT. בנוסף, ALM מספקת API לאוטומטיזציה של כל פונקציה זמינה בממשק המשתמש.

ניהול בעלות על משתמשי שירות
שלטו בגישה של משתמשים, בהגדרות ובתהליכי בקשת הרשאות וגישה באמצעות הרשאות מבוססות תפקידים (role-based access). השתמשו בתפקידים מוגדרים מראש כמו System Admin, Account Owner, Requesters ו-Approvers, וצרו תפקידים נוספים לפי הצורך לתמיכה בפונקציות עסקיות ספציפיות. ודאו עמידה במדיניות הפרדת תפקידים (SOD) על ידי הטמעת תהליך אישור שמתואם על ידי מנהלים.
![]()
הקצאת חשבונות (provisioning)
ודאו את הסדרת חשבונות השירות עם הקצאה אוטומטית. הקימו תבניות שמפרטות את פרוטוקולי יצירת החשבונות. אפשרו פירוק חלק של חשבונות שירות ללא הפרעות. צמצמו בצורה יעילה את התפשטות חשבונות השירות וחזקו את עמדת האבטחה שלכם.

ניטור ודיווח
הקימו אחריות ובעלות על חשבונות שירות. ערכו ביקורות קומפליינס בצורה חלקה באמצעות חיפושי חשבונות, דיווחים ופונקציות רישום. הישארו מעודכנים עם התראות שמשולבות ישירות בתהליך העבודה שלכם לפעולה מיידית.
Server Suite: תוכנת AD Bridging
שפרו את עמדת האבטחה על ידי אכיפת הרשאות Just-in-Time ו-Just-enough על שרתי Linux, Unix ו-Windows, המנוהלים בצורה מרכזית באמצעות מדיניות Active Directory.
השתמשו בטכנולוגיית ה-Zone המוגנת בפטנט של Delinea כדי לרכז גילוי, ניהול ומנהל משתמשים על מערכות Linux, Unix ו-Windows, מה שמפשט את איחוד הזהויות ל-Active Directory. אכפו רמות גבוהות יותר של אבטחת זהות וצמצום משמעותי במשטח ההתקפות, זהויות מיותרות וחשבונות מקומיים.
יכולות:

ניהול זהויות מממשק יחיד
נהל משתמשים/חשבונות שירות פריווילגיים ושירותים החוצים סביבות Windows ו-Linux ישירות בתוך Active Directory.

הפכו אותנטיקציה לפשוטה
הפכו את אימות המשתמשים לשרתי היעד לפשוט ללא טרחה על פני שירותי דירקטורי שונים, כולל Active Directory, Open LDAP וקטלוגים בענן כמו Azure AD, Okta או Ping. חזקו את אבטחת הגישה עבור מערכות ווירטואליות ומיכלים של Linux, Unix ו-Windows באמצעות MFA מחייב, מה שמבטיח הגברת אבטחת הזהות.

הקלטה וניטור
גלו ומנעו ניצול פריווילגיות, סכלו מתקפות זדוניות, והצגו בקלות את מצב הקומפליינס הרגולטורי באמצעות עקבות אודיט מפורטות והקלטות וידאו שתופסות כל פעילות פריווילגית. פשטו את הניתוח הוויזואלי עם הקלטות ניתנות לחיפוש לתהליכי חקירה מזורזים.

שליטה בהרשאות פריווילגיות
ודאו שמדיניות "המינימום הנדרש" תאכף על פני תשתיות Windows, Linux ו-UNIX הן בענן והן במערכות מקומיות, כולל מספר עננים. צמצמו את ההרשאות הקיימות כדי למנוע חדירות נתונים או מתקפות כופר פוטנציאליות על ידי עיכוב תנועת רוחב אופקי. למנהלים יש אפשרות לבקש העלאת הרשאות Just-in-Time (JIT) עבור פרקי זמן ספציפיים.
Gytpol: איתור ותיקון מיסקונפיגורציות בארגון
הסירו בצורה מאובטחת אזורים מתים באבטחת הארגון, וחזקו את האבטחה בלחיצת כפתור, ללא הפרעה לרצף העבודה.
מיסקונפיגורציות: מברירות מחדל לא נכונות ושגיאות בהגדרה ועד לאכיפת מדיניות לא מושלמת ופגיעויות שלא ניתן לתקן – הן גם נפוצות וגם יקרות. עקב פיצול תפעולי, הן גם קשות לזיהוי ולעיתים אף קשה יותר לתקן. עם Gytpol, אתם יכולים לבצע שינויים בביטחון ללא דאגה לפגוע במשהו. בנוסף, כל שינוי ניתן לביטול מידי בלחיצה.
יכולות:

איתור מיסקונפיגורציות
השתלטו על אבטחת נקודות הקצה המקומיות ויישמו גישה מבוססת מדיניות של "המינימום הנדרש". נהלו ביעילות משתמשים וקבוצות מקומיים, שלטו בהרשאות מנהל מקומי ואוטומטו את החלפת הסיסמאות. השתמשו ב-Privilege Manager כדי להסיר אוטומטית את כל ההרשאות המנהליות המקומיות בנקודות הקצה, ולהבטיח עמידה במדיניות "המינימום הנדרש". עם העלאת הרשאות ברמת היישום, משתמשים יכולים לגשת למערכות הדרושות להם מבלי לקבל הרשאות מוגבהות ברמת המשתמש.

תיקון חולשות באופן אוטומטי
Gytpol הופכת את התיקון לפשוט כמו לחיצה על כפתור (באמת!). באמצעות מיפוי תלויות (dependencies) בהגדרות, היא מאפשרת למשתמשים לבצע שינויים ורמידיאציות בביטחון וללא הפרעות. בנוסף, ניתן לשחזר לאחור כל שינוי באופן מיידי בלחיצה אחת.

אכפו מדיניויות מאובטחות
להגדיר מדיניות זו רק ההתחלה; לדעת שהיא מעוצבת ומיושמת כראוי זה המפתח. Gytpol עוזרת לכם להקים את קו הבסיס לאבטחה על פי בקרות זמינות ושיטות קונפיגורציה מיטביות, ומוודאת שהמדיניות נבנית ומאכפת כראוי ברחבי הרשת. עם תיאום מראש של מנגנוני האכיפה והחלת מדיניות דינמית על חברי קבוצות חדשים, Gytpol מסירה את כל חוסר הוודאות וההנחות.
